The Best VoIP Service for Small Business
For small businesses on the path to growth, adapting to change requires an overhaul in communication systems, namely to replace that plain old telephone service. VoIP (Voice Over Internet Protocol) services are a cost-effective and efficient alternative, providing you a flexible and scalable communication system. However, with so many options on the market, selecting the...
The Power of Managed IT Services for Tri-Copy Office Equipment
In today's fast-paced digital landscape, businesses of all sizes are constantly seeking ways to streamline operations, boost productivity, and stay ahead of the competition. For companies like Tri-Copy Office Equipment, which rely heavily on technology to drive their day-to-day operations, having a robust IT infrastructure is not just desirable – it's essential. Enter managed IT...
Navigating the Waters of Productivity with Refreshing Insights on Water and Ice
In the dynamic realm of office equipment, where productivity meets innovation, Tri-Copy Office Equipment has always been at the forefront. Today, we embark on a refreshing journey, exploring the often-overlooked elements of water and ice within the office environment. Join us as we dive into the significance of these essentials and discover how Tri-Copy brings...
Why You Should Choose Tri-Copy Office Equipment as Your Managed Service Provider
In the dynamic landscape of today’s business world, companies are continually seeking ways to enhance productivity, reduce costs, and stay ahead of the competition. One critical aspect of achieving these goals is optimizing office equipment and streamlining document management processes. This is where Tri-Copy Office Equipment emerges as a standout choice for companies searching for...
Unlocking Connectivity: The Importance of VoIP Services in the Modern World
In today’s fast-paced, interconnected world, communication lies at the heart of every successful business and personal relationship. As technology continues to evolve, traditional means of communication are being replaced by more efficient and cost-effective solutions. Voice over Internet Protocol (VoIP) services have emerged as a game-changer, revolutionizing the way we connect, communicate, and collaborate. This...
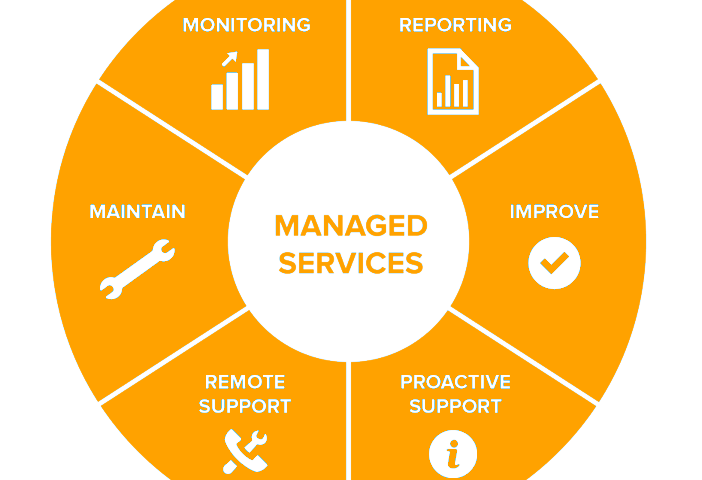
Elevating Your Business with Comprehensive Managed IT Support Services
In today’s fast-paced digital world, businesses of all sizes rely heavily on technology to operate efficiently and effectively. However, managing an IT infrastructure can be a daunting task, especially for small and medium-sized businesses. This is where comprehensive managed IT support services come into play. What Are Comprehensive Managed IT Support Services? Comprehensive managed IT...
Georgia’s Early Leadership To Prohibit Purchases of Dangerous China Tech Is An Example For Other States
Did you hear the news from China Tech Threat (CTT)? Georgia emerged as an early leader with the passage of SB 346 to protect Georgia residents from China intrusion. Authored by State Rep. Martin Momtahan and signed into law in 2022 by Governor Kemp, the law prohibits companies owned or operated by China from bidding on state contracts. This law was timely as CTT’s research...
What are the benefits of a Waterlogic system?
A Waterlogic system offers several benefits for providing clean and purified water. Here are some of the key advantages: 1. Advanced Filtration: Waterlogic systems utilize advanced filtration technologies to remove impurities, such as sediment, chlorine, heavy metals, bacteria, and viruses from tap water. This ensures that the water you consume is clean, safe, and free...
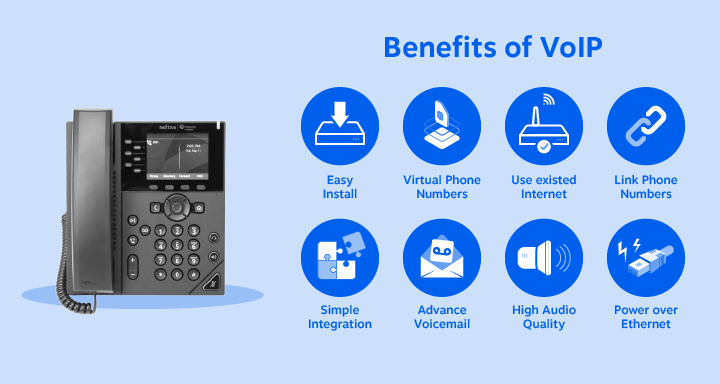
What are the top advantages of VoIP for businesses?
Voice over Internet Protocol (VoIP) offers several advantages for businesses. Here are some of the top advantages of VoIP: Cost Savings: VoIP can significantly reduce communication costs, especially for long-distance and international calls. Since VoIP utilizes the internet for transmitting voice data, it eliminates the need for traditional telephone lines, resulting in lower expenses for...
WL Ice 900
The WL Ice 900 is Tri-Copy's ultimate ice & water solution. The WL900 combines design with the latest technology. With a separate water delivery and a daily ice production of 44lbs, plus additional storage of 8lbs, this machine is perfect to cater for a high number of users. It’s the ideal choice for busy workplaces and environments. This dispenser utilizes reverse osmosis...